Search for "sec" returned 2714 results
133 min
Einmal Stasi – immer Stasi?
Der „Fall Andrej Holm“ und der gesellschaftliche Umgang mit…

63 min
Analyze the Facebook algorithm and reclaim data sovereignty
Algorithms define your priorities. Who else besides you can…
62 min
Cryptocurrency Hardware Wallets
Building the First Monero Hardware Wallet

60 min
What the PHUZZ?!
Finding 0-days in Web Applications with Coverage-guided…

61 min
Quantenphysik und Kosmologie
Eine Einführung für blutige Anfänger
53 min
DG112: Wer hat den kleinsten Anhang?
Erste Hilfe für sinnvolle Mediendateigrößen
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…
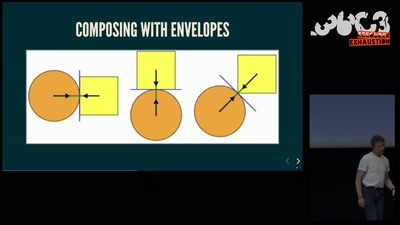
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!

60 min