Search for "Ron" returned 9417 results

57 min
“I feel like a criminal and I have to be god at the same time”
Perceptions of hackers and hacktivists on their…

21 min
Another Approach to AI
An approach to ethical AI focussed on transparency and…

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

39 min
Analog Computing
High performance/low power computing based on the analog…
138 min
Enemies of the State: What Happens When Telling the Truth about Secret US Government…
Blowing the Whistle on Spying, Lying & Illegalities in the…
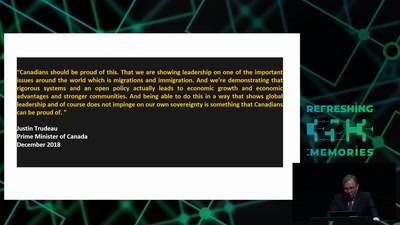
59 min
The Surveillance State limited by acts of courage and conscience
An update on the fate of the Snowden Refugees
64 min
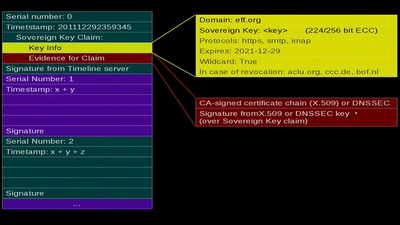
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC

50 min
Creating printable maps
From OpenStreetMap data to large scale maps on paper
47 min
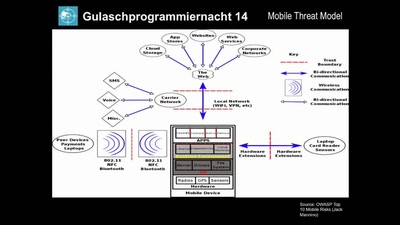
All your secrets belong to me
Why you shouldn't store secrets on a mobile device
51 min
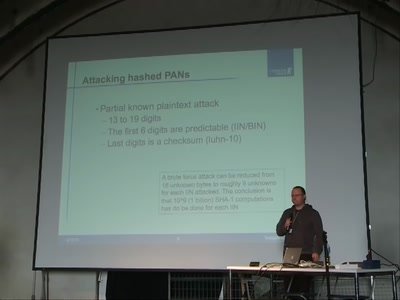
Strong encryption of credit card information
Attacks on common failures when encrypting credit card…

57 min
Aus der Debian Appliance in die Deutsche Verwaltungscloud - behalten oder neu machen?
Migration bestehender Softwarestrukturen in DVS konforme…

50 min
Connected Mobility hacken: digital.bike.23
Von E-Bikes in der Connected Mobility zur Entstehung eines…
52 min
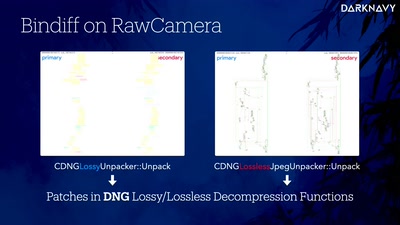
DNGerousLINK
A Deep Dive into WhatsApp 0-Click Exploits on iOS and…
59 min
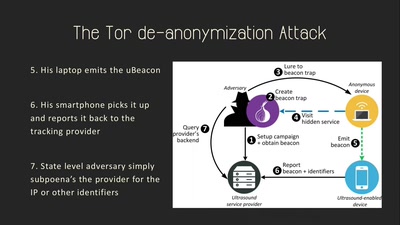
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…

37 min
Creating printable maps
From OpenStreetMap data to large scale maps on paper
49 min
Future 3.0
One Theory on Patterns in Culture, Technology and Commerce

61 min
The A5 Cracking Project
Practical attacks on GSM using GNU Radio and FPGAs
25 min
Uyuni: introduction, last year's updates and future
What is Uyuni? - What's been going on the last year? -…

50 min