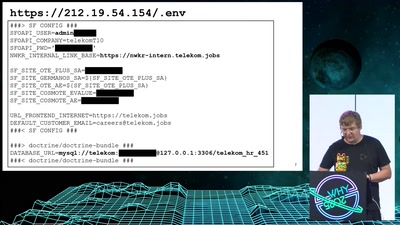
Search for "Kay" returned 3816 results

60 min
Kybernetik und Kontrolle
Von der autoritären Nutzung von Daten in China und anderswo

60 min
Let's talk about Desktop Linux Platform Issues
What's holding back Linux on the desktop?

55 min
Attribution revolution
Turning copyright upside-down with metadata
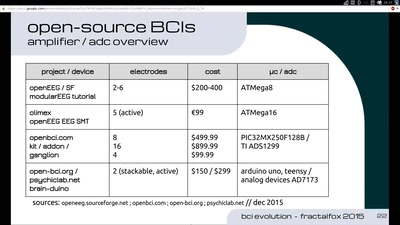
35 min
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…
8 min
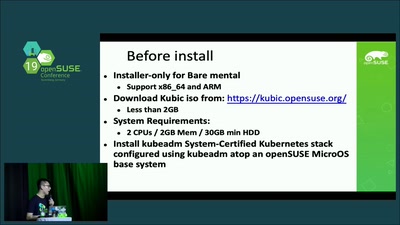
Why you should choose openSUSE Kubic?
openSUSE Kubic is really fun!
60 min