Search for "CAGE" returned 2826 results

53 min
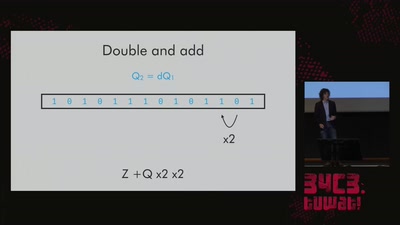
From Maxwell to antenna arrays
How 150 year old equations still help to communicate

72 min
Console Hacking
Breaking the 3DS

60 min
Dieselgate – A year later
env stinks || exit
61 min
Avoiding kernel panic: Europe’s biggest fails in digital policy-making
How the institutions fuck up, and how we fuck it up as well
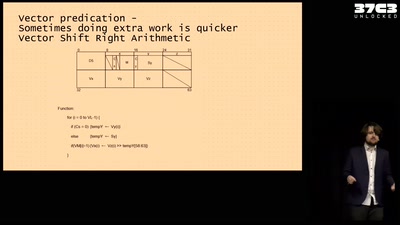
39 min
Making homebrew for your very own Vector Super Computer
Adventures running a NEC Vector Engine for fun and ...…

58 min
Taming the Chaos: Can we build systems that actually work?
Possible paths from today's ghastly hackery to what…

33 min
UPSat - the first open source satellite
Going to space the libre way
48 min
10 Years of Fun with Embedded Devices
How OpenWrt evolved from a WRT54G firmware to an universal…

60 min
Crypto Wars Part II
The Empires Strike Back

26 min
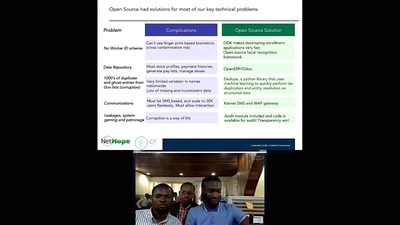
Data Mining for Good
Using random sampling, entity resolution, communications…
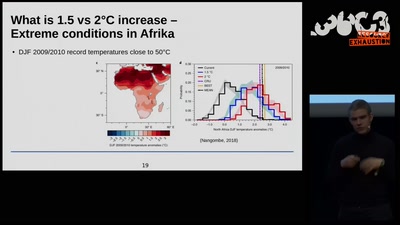
63 min
Science for future?
What we can and need to change to keep climate change low -…
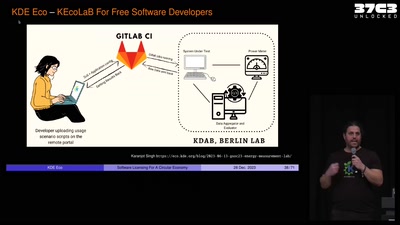
40 min
Software Licensing For A Circular Economy
What's FOSS Got To Do With It

56 min
Viva la Vita Vida
Hacking the most secure handheld console

54 min
What Price the Upload Filter?
The history and costs of government exceptional access

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks
66 min
Hacking Diversity: The Politics of Inclusion in Open Technology Cultures
Christina Dunbar-Hester
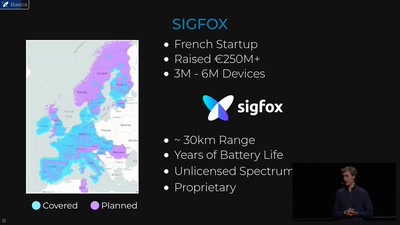
38 min