Search for "CAGE" returned 2827 results

14 min
c3 NewsShow
Tag 1

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

58 min
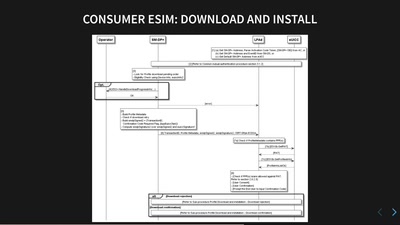
How to Break PDFs
Breaking PDF Encryption and PDF Signatures
32 min
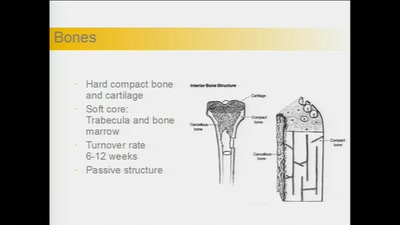
Coding your body
How to decipher the messages of your body
33 min
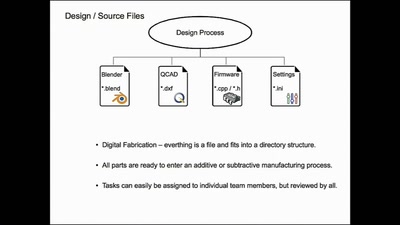
Structuring open hardware projects
experiences from the “i3 Berlin” 3D printer project with…
35 min
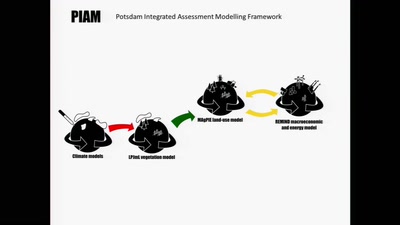
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…
60 min
Netzpolitik in der Schweiz
NDG, BÜPF und wie wir uns dagegen wehren
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
59 min
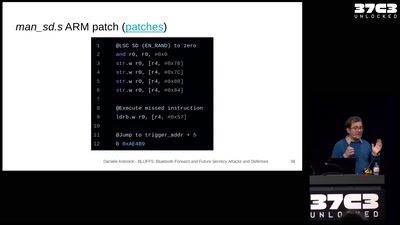
BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses
Breaking and fixing the Bluetooth standard. One More Time.

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

58 min