Search for "Mo" returned 9996 results

29 min
Jumping the Paywall
How to freely share research without being arrested

46 min
Atmel AVR für Dummies
Was ist denn nun eigentlich so ein 'Interrupt'?

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

108 min
Open Emacs Workshop (join anytime)
An introduction to the Lispers' editor of choice
42 min
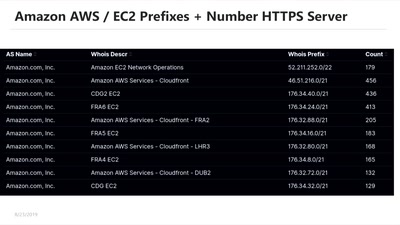
Fast Global Internet Scanning - Challenges and new Approaches
Or how to become your own ISP
29 min
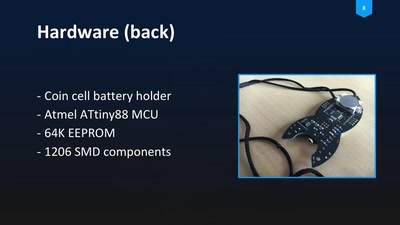
Blinkenrocket!
How to make a community project fly
25 min
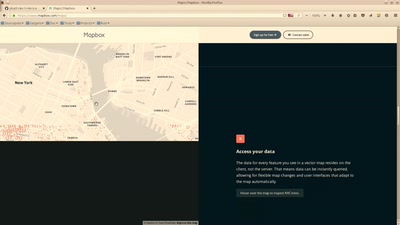
Von WMS zu WMTS zu Vektor-Tiles
Eigene Daten als MB Vektor-Tiles publizieren

30 min
NFCGate - NFC security analysis with smartphones
Use your smartphone to relay NFC data

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

61 min
The Realtime Podcast
Everything you need to know about Podcasting

38 min
Multi-Model NoSQL Databases
An introduction to Polyglot persistence and NoSQL
51 min
EFI Rootkits
Abusing your Firmware to backdoor the kernel
61 min
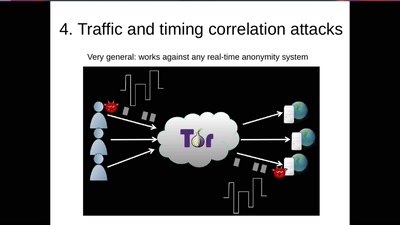
Tor de-anonymization techniques
How people have lost their anonymity? Let's study…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

37 min
E-Commerce – Greening the Mainstream
Wie können Amazon & Co. ökologischer und sozialer werden?

20 min
HTCPCP - Networking your Coffeepot
IoT done right for fun and no profit

41 min
privacyIDEA
Die Open Source Alternative zu RSA SecurID & Co.
43 min
Artist Talk
We Show You What You Want To See

50 min
Modern Software Packaging for Developers
Wait, how to install your FOSS project again?

35 min