Search for "Steve" returned 223 results

61 min
Running your own GSM stack on a phone
Introducing Project OsmocomBB

42 min
Covert channels in TCP/IP: attack and defence
Creation and detection of IP steganography for covert…

62 min
Detecting temperature through clock skew
Hot or Not: Defeating anonymity by monitoring clock skew to…
62 min
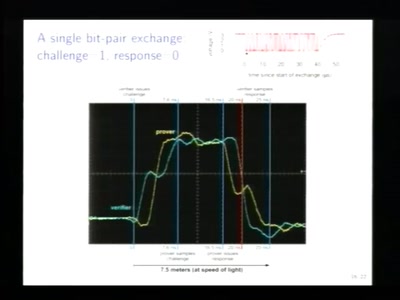
Relay attacks on card payment: vulnerabilities and defences
Keeping your enemies close

45 min
The Convergence of Anti-Counterfeiting and Computer Security
Reverse-engineering currency detection systems
57 min
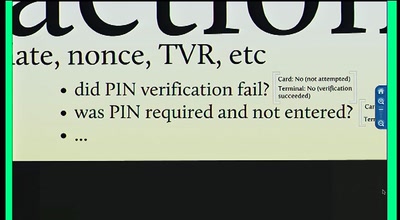
Chip and PIN is Broken
Vulnerabilities in the EMV Protocol

58 min
Security Failures in Smart Card Payment Systems
Tampering the Tamper-Proof

46 min
Have you hugged your Mac today?
Ein audiovisuelles Live-Feature

61 min

![osmo-fl2k - the [evil] transmit-side brother of RTL-SDR](https://static.media.ccc.de/media/events/osmocon/2018/83-hd.jpg)