Search for "Hugo" returned 771 results
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…

61 min
Uncaging Microchips
Techniques for Chip Preparation

46 min
The nextpnr FOSS FPGA place-and-route tool
the next step forward in open source FPGA tools
59 min
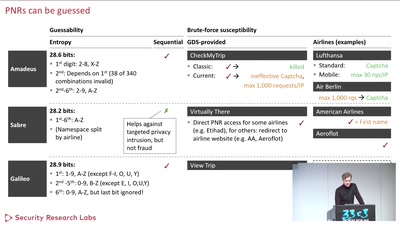
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14

58 min
Baseband Exploitation in 2013
Hexagon challenges

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

63 min
Traue keinem Scan, den du nicht selbst gefälscht hast
"Bei Kopierern kommt das raus, was man reinsteckt." – Wer…

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

57 min