Search for "Mark" returned 1137 results
62 min
Space Hacker
Uploading rover...

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice
43 min
Seeds of Change
Unlearning & Radical Collective Change in Online Communities

39 min
Hurra, diese Welt geht unter!?
Welche kollektiven Erzählungen brauchen wir, um in der…

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
55 min
Lobby-Schlacht um die ePrivacy-Verordnung
Die EU hat die Wahl: Schutz von Menschen oder von…

115 min
Hacker Jeopardy
Zahlenraten für Geeks
58 min
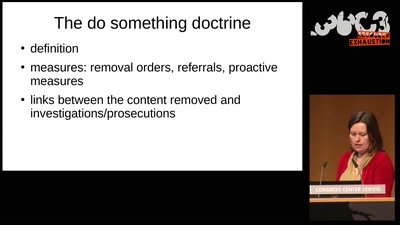
Confessions of a future terrorist
A rough guide to over-regulating free speech with…

39 min
DISNOVATION.ORG
Disobedient Innovation
99 min
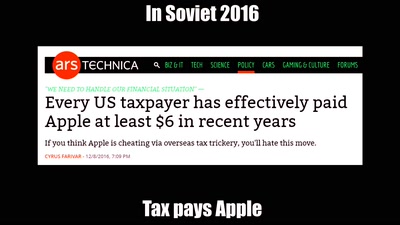
Fnord-Jahresrückblick
Wir helfen euch, die Fnords zu sehen!

45 min
To Protect And Infect
The militarization of the Internet
62 min
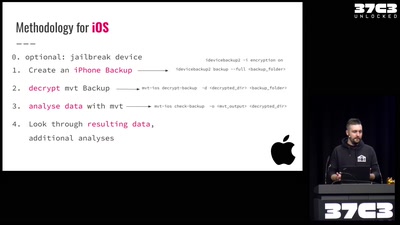
Einführung in Smartphone Malware Forensik
Wie man Stalkerware und Staatstrojaner auf Smartphones…

48 min
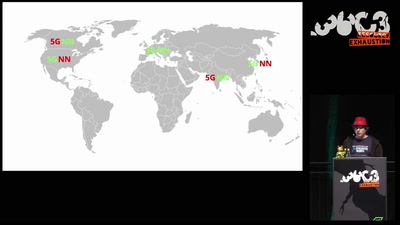
Seidenstraße
The Making of…
42 min