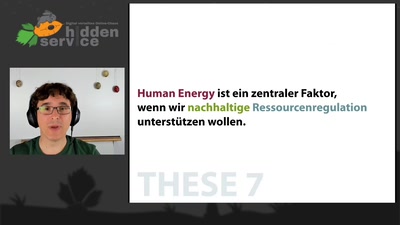
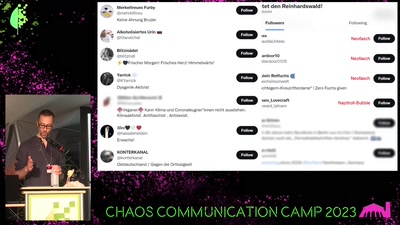
Search for "Jakob" returned 125 results

41 min
Back in the Driver's Seat
Recovering Critical Data from Tesla Autopilot Using Voltage…
119 min
monochrom's Taugshow #12
A joyful bucket full of good clean fanaticism, crisis,…

65 min
Building an international movement: hackerspaces.org
What we did so far. What will happen in the future.

61 min
MD5 considered harmful today
Creating a rogue CA Certificate

45 min
To Protect And Infect
The militarization of the Internet

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

60 min