Search for "Ben" returned 8971 results

61 min
SMS-o-Death
From analyzing to attacking mobile phones on a large scale.

63 min
Power gadgets with your own electricity
escape the basement and make the sun work for you

62 min
Automatic Algorithm Invention with a GPU
Hell Yeah, it's rocket science

82 min
Attacking NFC mobile phones
First look at the security of NFC mobile phones

38 min
Steam-Powered Telegraphy
A League of Telextraordinary Gentlemen present the marvel…

49 min
Lawful Interception in VoIP networks
Old Laws and New Technology the German Way
67 min
Life is a Holodeck!
An overview of holographic techniques

61 min
Defend your Freedoms Online: It's Political, Stupid!
A Positive agenda against the next ACTA, SOPA, and such
40 min
The Joy of Intellectual Vampirism
Mindfucking with Shared Information

63 min
Wireless Kernel Tweaking
or how B.A.T.M.A.N. learned to fly
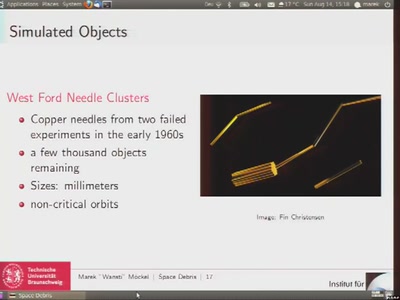
50 min
Space Debris
Simulation of orbital debris and its impacts on space travel

83 min
Fnord-Jahresrückblick 2010 (english translation)
von Atomausstieg bis Zwangsintegration

63 min
She-Hackers: Millennials and Gender in European F/LOSS Subcultures
A Presentation of Research and Invitation for Debate

49 min
Applied Machine Learning
Brief Introduction into Machine Learning followed by…
55 min
FrozenCache
Mitigating cold-boot attacks for Full-Disk-Encryption…

44 min
Open Source Machine Translation
From tools, to tricks, to projects: build a translation…

59 min
Vulnerability markets
What is the economic value of a zero-day exploit?
43 min
Lightning Talks Day 1
Nine five minutes talks by various speakers

59 min
Safety on the Open Sea
Safe navigation with the aid of an open sea chart.

48 min
Let Me Answer That for You
adventures in mobile paging
51 min
SCADA and PLC Vulnerabilities in Correctional Facilities
Tiffany Rad, Teague Newman, John Strauchs

58 min


