43 min
How Facebook tracks you on Android
(even if you don’t have a Facebook account)

51 min
Smart Home - Smart Hack
Wie der Weg ins digitale Zuhause zum Spaziergang wird

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende
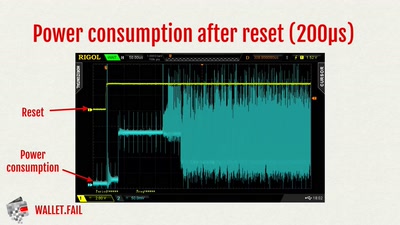
61 min
wallet.fail
Hacking the most popular cryptocurrency hardware wallets

67 min
Freude ist nur ein Mangel an Information
Ein Demotivationsworkshop zur politischen Lage.
61 min
Verhalten bei Hausdurchsuchungen
Praktische Hinweise für den Kontakt mit der Staatsmacht
46 min
What The Fax?!
Hacking your network likes it's 1980 again
62 min
The Ghost in the Machine
An Artificial Intelligence Perspective on the Soul

39 min
Venenerkennung hacken
Vom Fall der letzten Bastion biometrischer Systeme

40 min
Hackerethik - eine Einführung
Verantwortung und Ethik beim schöpferisch-kritischen Umgang…

61 min
"The" Social Credit System
Why It's Both Better and Worse Than We can Imagine

26 min
Opening Event
35C3: Refreshing Memories

135 min
Jahresrückblick des CCC 2018
Refreshing Memories
41 min
Archäologische Studien im Datenmüll
Welche Daten speichert Amazon über uns?

60 min
Best of Informationsfreiheit
Transparenz mit der Brechstange
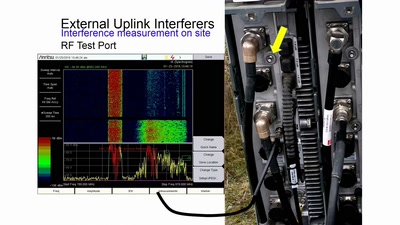
60 min
Die verborgene Seite des Mobilfunks
HF-Störquellen im Uplink

61 min
All Your Gesundheitsakten Are Belong To Us
"So sicher wie beim Online-Banking": Die elektronische…

58 min
Polizeigesetze
Endlich viele neue Gründe zu demonstrieren
32 min
Internet of Dongs
A long way to a vibrant future
37 min
Inside the AMD Microcode ROM
(Ab)Using AMD Microcode for fun and security

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

57 min
The Precariat: A Disruptive Class for Disruptive Times.
Why and How the Precariat will define the Global…

59 min
How to teach programming to your loved ones
Enabling students over example-driven teaching

52 min
SiliVaccine: North Korea's Weapon of Mass Detection
How I Learned to Stop Worrying and Love the Backdoor

62 min
Space Ops 101
An introduction to Spacecraft Operations

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

58 min
Funkzellenabfrage: Die alltägliche Rasterfahndung unserer Handydaten
Wie wir alle regelmäßig den Behörden ins Netz gehen und wie…

61 min
Safe and Secure Drivers in High-Level Languages
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…
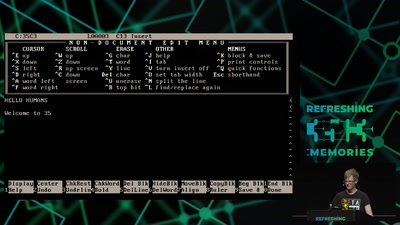
38 min
A deep dive into the world of DOS viruses
Explaining in detail just how those little COM files…
37 min
Butterbrotdosen-Smartphone
Mein DIY-Smartphone-Bau
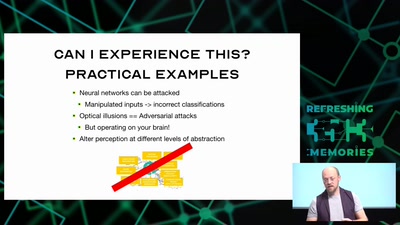
58 min
Hacking how we see
A way to fix lazy eye?

56 min
Viva la Vita Vida
Hacking the most secure handheld console
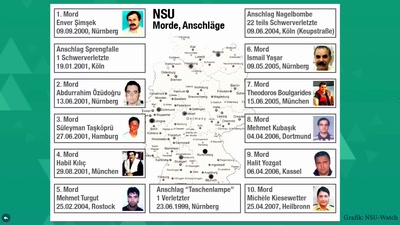
63 min
"Das ist mir nicht erinnerlich." − Der NSU-Komplex heute
Fünf Monate nach dem Urteil im ersten NSU-Prozess

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.
39 min
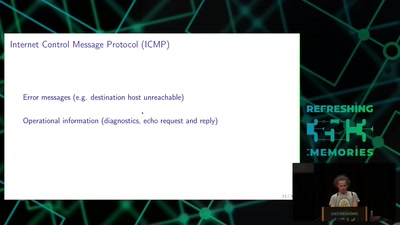
Transmission Control Protocol
TCP/IP basics

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

60 min
LibreSilicon
Decentralizing semiconductor manufacturing

36 min
Modchips of the State
Hardware implants in the supply-chain

62 min
Was schützt eigentlich der Datenschutz?
Warum DatenschützerInnen aufhören müssen von individueller…
43 min
The Mars Rover On-board Computer
How Curiosity's Onboard Computer works, and what you can…

41 min
Locked up science
Tearing down paywalls in scholarly communication

41 min
Frontex: Der europäische Grenzgeheimdienst
Das Grenzüberwachungssystem EUROSUR führt Aufklärungsdaten…
38 min
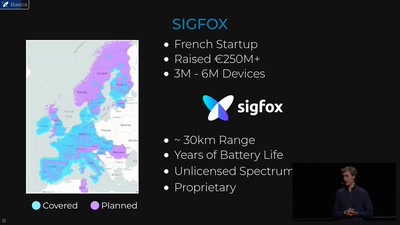
Hunting the Sigfox: Wireless IoT Network Security
Dissecting the radio protocol of Sigfox, the global…
44 min
Stalking, Spy Apps, Doxing: Digitale Gewalt gegen Frauen
Die digitale Seite der häuslichen Gewalt
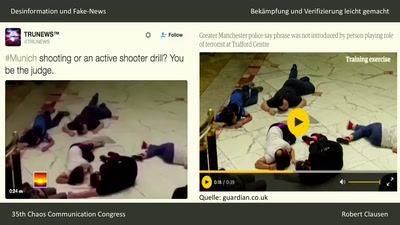
42 min
Desinformation und Fake News
Bekämpfung und Verifizierung leicht gemacht

49 min
Open Source Firmware
Eine Liebesgeschichte
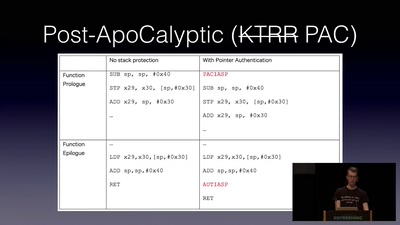
47 min
Jailbreaking iOS
From past to present

44 min
Genom-Editierung mit CRISPR/Cas
“Eine neue Hoffnung” oder “Angriff der Klonkrieger”?

34 min
Scuttlebutt
The decentralized P2P gossip protocol
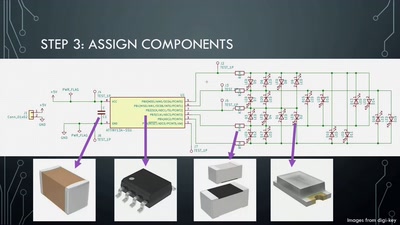
36 min
Artistic PCB Design and Fabrication
From doodle to manufacture: how I make mechanically…
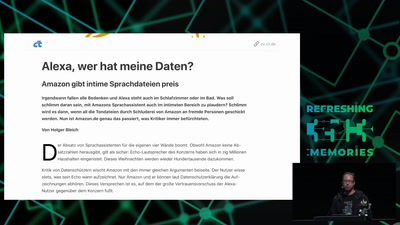
42 min
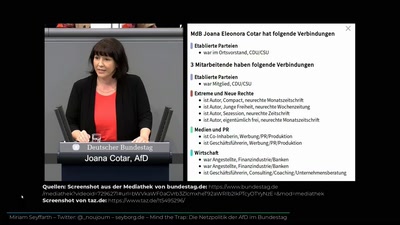
Netzpolitischer Wetterbericht 2018
Die Höhen und Tiefen der deutschen und europäischen…
57 min
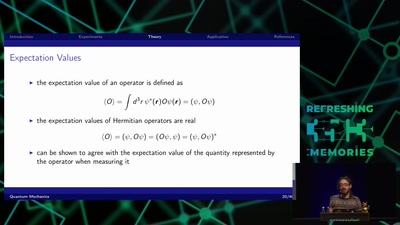
Quantum Mechanics
A Gentle Introduction

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

40 min
Radical Digital Painting
Fantastic Media Manipulation

41 min
MicroPython – Python for Microcontrollers
How high-level scripting languages make your hardware…
58 min
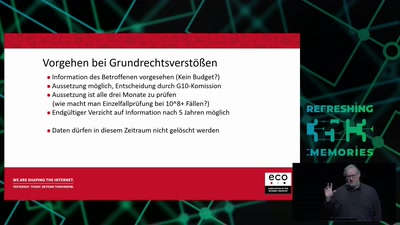
G10, BND-Gesetz und der effektive Schutz vor Grundrechten
Die strategische Fernmeldeüberwachung des BND vor dem…

101 min
Chaos Communication Slam
Technische Liebesgedichte & Horrorgeschichten im…
59 min
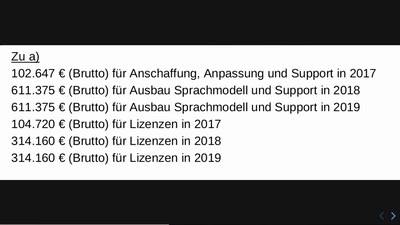
Computer, die über Asyl (mit)entscheiden
Wie das BAMF seine Probleme mit Technik lösen wollte und…

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…

58 min
Taming the Chaos: Can we build systems that actually work?
Possible paths from today's ghastly hackery to what…

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux
41 min
A WebPage in Three Acts
live coding performance

43 min
Microtargeting und Manipulation
Von Cambridge Analytica zur EU-Wahl
65 min
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…

60 min
A farewell to soul-crushing code
Towards correct software that enriches our lives
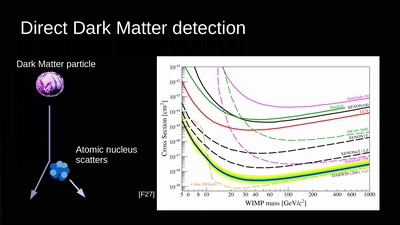
60 min
Let's reverse engineer the Universe
exploring the dark

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…

68 min
#afdwegbassen: Protest, (Club-)Kultur und antifaschistischer Widerstand
Über kreative Organisation, poltische Aktionen und das…
40 min
Court in the Akten
OpenSchufa und OffeneGesetze
62 min
SuperMUC-NG
… und das Rennen um den schnellsten Computer der Welt
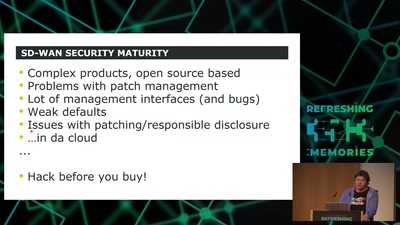
49 min
SD-WAN a New Hop
How to hack software defined network and keep your sanity?

36 min
A Blockchain Picture Book
Blockchain origins and related buzzwords, described in…
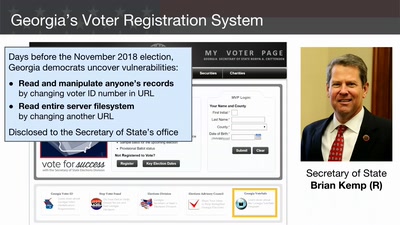
59 min
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?
54 min
How medicine discovered sex
Introduction to sex- and gender-sensitive medicine

41 min
Österreich: Überwachungsstaat oder doch nur Digitalisierung für Anfänger?
Ein Jahr unter der rechtsextremen Regierung
35 min
Wallet Security
How (not) to protect private keys

46 min
Digital Airwaves
Software Defined Radio Basics and some Modulation Theory

42 min
All Creatures Welcome
a utopian documentary about the digital age
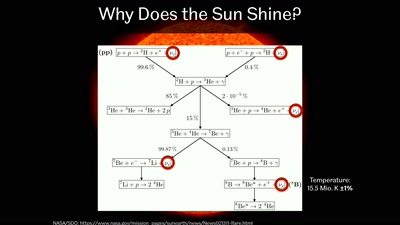
47 min
Going Deep Underground to Watch the Stars
Neutrino Astronomy with Hyper-Kamiokande

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

59 min
Provable Security
How I learned to stop worrying and love the backdoor
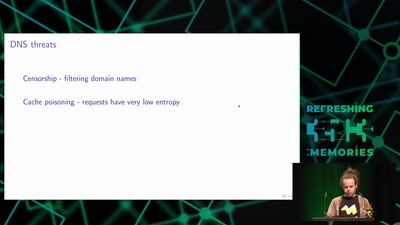
42 min
Domain Name System
Hierarchical decentralized naming system used since 30 years

43 min
Repair-Cafés
… und warum ihr dabei mitmachen solltet
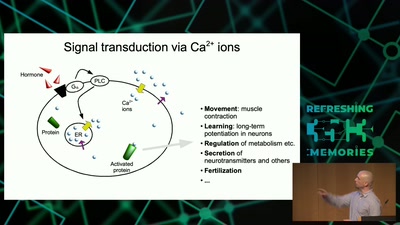
37 min
Information Biology - Investigating the information flow in living systems
From cells to dynamic models of biochemical pathways and …

41 min
Die Häuser denen, die darin wohnen!
Langfristig bezahlbares, gemeinsames „Mieteigentum“…
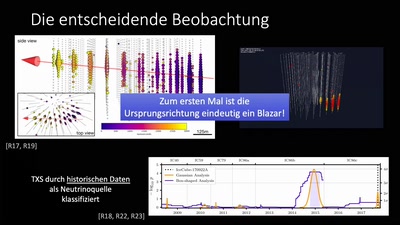
49 min
Kosmische Teilchenbeschleuniger und ihre Spuren in der Antarktis
Über die Identifikation des ersten kosmischen…
37 min
Schweiz: Netzpolitik zwischen Bodensee und Matterhorn
Massenüberwachung, Netzsperren und andere netzpolitische…

60 min
Are machines feminine?
exploring the relations between design and perception of…

62 min
SymbiFlow - Finally the GCC of FPGAs!
A fully FOSS, Verilog to bitstream, timing driven, cross…
60 min
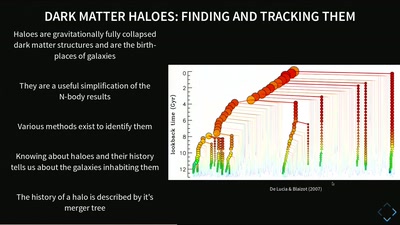
Simulating Universes
What Virtual Universes Can Tell Us About Our Own
60 min
Freedom needs fighters!
Wie die GFF mit strategischen Klagen für Freiheitsrechte…
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

77 min
Feminist Perspectives
Inclusive and Diverse Spaces and Communities

63 min
Analyze the Facebook algorithm and reclaim data sovereignty
Algorithms define your priorities. Who else besides you can…
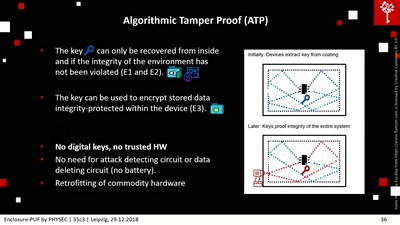
61 min
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications

55 min
What is Good Technology?
Answers & practical guidelines for engineers.
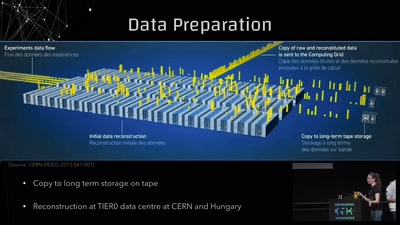
41 min
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

38 min
Kickstart the Chaos: Hackerspace gründen für Anfänger
Ein Erfahrungsbericht aus unbetreuter Vereinsmeierei
55 min
The good, the strange and the ugly in 2018 art &tech
On art, AI, hormones hacking and other prospects of a…
40 min
Never Forgetti
a didactic live-gaming performance about dying women across…
62 min
Internet, the Business Side
a try to explain the ecosystem
60 min
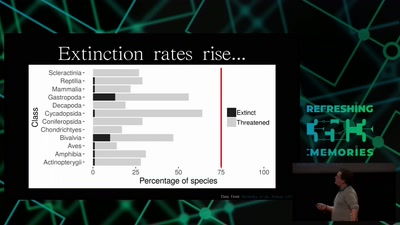
Hacking Ecology
How Data Scientists can help to avoid a sixth global…
61 min
Projekt Hannah
Ein open-source Hardware- und Software-Design für…
38 min
Modeling and Simulation of Physical Systems for Hobbyists
Essential Tools for Developing, Testing and Debugging…

46 min
The nextpnr FOSS FPGA place-and-route tool
the next step forward in open source FPGA tools
42 min
Citzens or subjects? The battle to control our bodies, speech and communications
A call to action to defend our ePrivacy and eliminate…

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online

57 min
Theater und Quantenzeitalter
„Die Parallelwelt“- Das Schauspiel Dortmund und die…

29 min
The Urban Organism
Hacking [in] Hong Kong
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…

56 min
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…
59 min
The Surveillance State limited by acts of courage and conscience
An update on the fate of the Snowden Refugees

46 min
Remo2hbo -Robustes und reparierbares Vitalparametermonitoring
Medizingeräte für Alle

54 min
A la recherche de l'information perdue
some technofeminist reflections on Wikileaks

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

60 min
The Critical Making Movement
How using critical thinking in technological practice can…

39 min
DISNOVATION.ORG
Disobedient Innovation

38 min
Afroroutes: Africa Elsewhere
VR experience "Beyond Slavery"

62 min
Transhuman Expression
Interdisciplinary research in Painting and Robotics. with…

49 min
C2X: The television will not be revolutionized.
From Cyberfeminism to XenoFeminism
31 min
Media Disruption Led By The Blind
Hacking Visual Culture

56 min